ISO/IEC 27001 Certification - Information Security Management System (ISMS)
ISO 27001 Certification(Information security Management System) – trust is a strong word make your words matter and be secured with an information security management system
- ISO 27001 certification enlists internationally accepted standards for establishing Information security Management System (ISMS) in your organization. It helps you to manage security risks to the information that you hold. ISO 27001 certification gives confidence to your clients, customers, and other stakeholders about your ability to protect information. This standard enables your organization to adopt a process-based approach for building, executing, operating, monitoring, maintaining, and improving your ISMS.
- ISO 27001 Certification helps the organizations in protecting valuable information within their premises by providing them the necessary know-how of the processes and activities to protect the information.
What is ISMS ISO 27001 Certification ?
ISO 27001 certification is an international standard that provides requirements for an information security management system (ISMS). Organizations that implement an ISMS can be certified by an accredited certification body.
An ISMS is a framework of policies and procedures that includes all legal, physical and technical controls involved in an organization’s information risk management processes. ISO 27001 certification demonstrates that an organization has implemented an ISMS in line with international best practices.
Organizations certified to ISO 27001 must undergo regular audits to ensure that their ISMS continues to meet the requirements of the standard. Certification is valid for three years and can be renewed indefinitely.
How to get ISO 27001 Certified
There are a few steps you need to take in order to get your organization ISO 27001 certified.
1. The first step is to develop your organization’s information security management system (ISMS). This system should be tailored to the specific needs of your organization and include all aspects of information security, from Policies and Procedures to Risk Management.
2. Once your ISMS is developed, you will need to have it audited by an accredited certification body. This audit will ensure that your ISMS meets all the requirements of the ISO 27001 standard.
3. Once you have passed the certification audit, you will be issued an ISO 27001 certificate, which is valid for three years. In order to maintain your certification, you will need to undergo annual surveillance audits and recertification audits every three years.
The Benefits of ISO 27001 Certification
@siscertifications.com
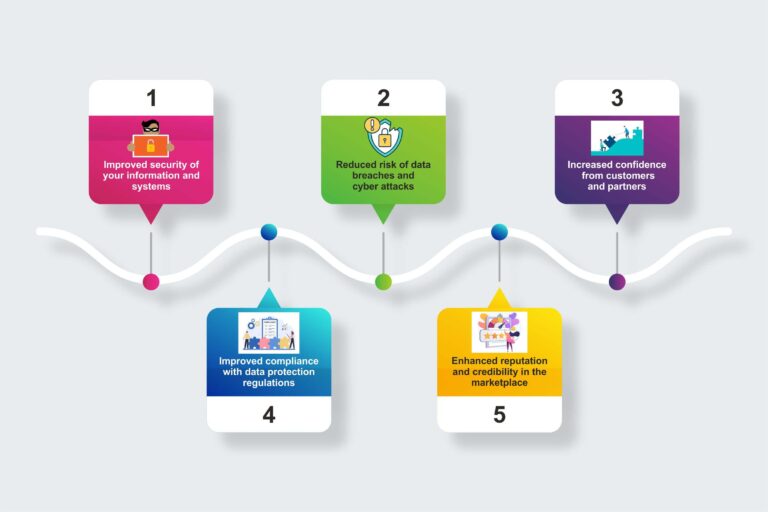
As the world becomes increasingly digital, the need for robust information security grows. ISO 27001 is the international standard that provides a framework for an effective Information Security Management System (ISMS). ISO 27001 demonstrates that your organization takes information security seriously and is committed to protecting your data.
Achieving certification requires a comprehensive approach to information security, covering people, processes and technology. The ISO 27001 benefits of certification will be felt across your entire organization, from the boardroom to the frontline. Your customers and partners will have increased confidence in your ability to keep their data safe, while you reap the rewards of reduced risk and improved compliance.
What's required for ISO 27001 Information Security Management System Certification (ISMS) ?
In order to be certified to ISO 27001, organizations must meet the requirements outlined in the standard. This includes having a documented Information Security Management System (ISMS) in place that covers all aspects of security, from risk assessment and treatment to incident management. The ISMS must be implemented and maintained according to the ISO 27001 standard, and the organization must be able to demonstrate its compliance through an external audit.
Tips for maintaining ISMS ISO 27001 Certification
There are a few key things to keep in mind when working towards and maintaining ISO 27001 certification :-
1. Keep your documentation up to date and accurate. This includes your security policy, risk assessment, and any procedures or controls you have in place.
2. Make sure all employees are aware of the importance of compliance and security, and that they understand their roles and responsibilities in relation to ISO 27001.
3. Regularly review your security posture and make sure you are taking steps to address any identified risks.
4. Maintain an incident response plan so you know how to deal with any potential security breaches.
By following these tips, you can help ensure that your organization remains compliant with ISO 27001 and keeps its certification status.
What are the major changes in ISO/IEC 27001:2022 in 2022
Some of the main new updates of ISO/IEC 27001:2022 include a major change of Annex A, minor updates of the clauses, and a change in the title of the standard. The latest version of ISO/IEC 27002 has been published at the beginning of 2022, and its latest changes have also impacted ISO/IEC 27001.
Requirements of ISO 27001 Certifications
- Context to the Organization
Existing – Context to the Organization – It requires an organization to define the scope of ISMS and identify all the internal and external issues related to its information security and the expectations of the interested parties.
New – Context to the Organization – An organization must understand the context of the organization and define its scope to establish an effective Information Security Management System. The latest update requires an organization to identify only the relevant requirements, which will be addressed through the Information Security Management System (ISMS).
- Planning
Existing –It requires an organization to define its information security objectives based on the risk assessment and implement appropriate controls listed in Annex A. It determines plans and actions to address risks and opportunities and prepares a Statement of Applicability (SoA).
New – An organization requires defining its information security objectives based on the risk assessment and implementing appropriate controls listed in Annex A. It also requires documenting the available information and determining plans and actions to address risks and opportunities and preparing a Statement of Applicability (SoA).
- Support
Existing – It focuses on the competence of personnel, resources, people and infrastructure and establishes sound communication, including external and internal, to establish a sound ISMS. It provides necessary training to the employees and requires documenting information related to information security.
New – It aims to enhance the competence of personnel, resources, people and infrastructure and establishes sound communication, including external and internal, to establish a sound ISMS. An organization shall focus on “how to communicate” rather than “who will communicate.”
- Operation
Existing – This clause works in line with Clause 6 and focuses on the execution of all the plans and processes. It outlines the outcomes of the risk assessment and requires maintaining all the related documents. It focuses on implementing risk assessment and treatment plans to establish an efficient Information Security Management System.
New – This clause works in line with Clause 6. The latest update replaces the requirements to plan how to achieve the information security objectives with establishing criteria for processes to implement the actions identified in the planning clause. An organization must control its external processes, products, and services related to ISMS.
- Performance Evaluation
Existing – It requires an organization to monitor, measure, analyze and evaluate the ISMS to ensure its effectiveness and efficiency. It evaluates the organization’s performance to the defined objectives. This clause also requires an organization to conduct internal audits to review its Information Security Management System (ISMS).
New – An organization shall adopt comparable and reproducible methods to monitor, measure, analyze and evaluate the ISMS to ensure its effectiveness and efficiency. It evaluates the organization’s performance to the defined objectives. This clause also requires an organization to conduct internal audits to management review to measure its Information Security Management System (ISMS) and make necessary changes to meet the needs and requirements of interested parties.
Annex A Security Control
New – The number of Annex A Security Controls is reduced from 114 to 93 controls. These controls are further divided into 4 themes rather than 14 domains.
- People (8 controls)
- Organizational (37 controls)
- Technological (34 controls)
- Physical (14 controls)
The new ISO 27001:2022 version introduces 11 new controls to the Annex A Security Control list. These new controls are:-
- Threat Intelligence
- Information Security for the Use of Cloud Services
- ICT Readiness for Business Continuity
- Physical Security Monitoring
- Configuration Management
- Information Deletion
- Data Masking
- Data Leakage Prevention
- Monitoring Activities
- Web Filtering
- Secure Coding
Existing –
ISO 27001 Annex A Controls or ISO 27001 controls . They are grouped into 14 domains. These are:-
- Information Security Policies
- Organization of Information Security
- Human Resources Security
- Asset Management
- Access Control
- Cryptography
- Physical and Environmental Security
- Operational Security
- Communications Security
- System Acquisitions, Development and Maintenance
- Supplier Relationships
- Information Security Incident Management
- Information Security Aspects of Business Continuity Management
- Compliance
PDCA Cycle
- Plan – to think that what do we need to achieve in our organization
- Do – to execute a planned action which will help us achieve the required objective
- Check – monitor against the standards) (policies, objectives, requirements)
- Action – finally implementing what has been rechecked.
How SIS Certifications can help you
ISO 27001 certification is a great way to show your commitment to security and demonstrate that you have implemented best practices. Getting certified can be a complex process, but it is well worth the effort to ensure that your organization is protected against potential threats. Our team of experts can help you navigate the certification process and ensure that you are prepared for success. Contact us today to learn more about how we can help you get ISO 27001 certified.
Contact Us
Frequently Asked Questions (FAQs) about ISO 27001
Answer: In the year 2022 the average global data breach cost was around $4.35 million which meant companies lack the necessary strategy to prevent their data from possible threats. ISO 27001 being a single part of the ISO 27000 family of security standards enables the integration of full-fledged ISMS within an organization. It addresses how organizations establish, maintain, monitor, and improve their ISMS to secure their data, documents, and other information assets.
Answer: ISO/IEC 27001 is an international standard that helps in the effective implementation of enterprise-wide Information Security Management System (ISMS) which is an organized way to maintain confidentiality and integrity within an organization. Along the same lines, ISO 27000 is a series of best practices to help organizations improve their information security management systems.
Get your organization certifications
The implementation of ISMS using ISO 27001 standard entails the following benefits for the organization:
Fulfill the legal obligations: ISO 27001 helps in complying with a large number of guidelines, laws, and other regulatory requirements of the land.
Gives you a competitive edge: by gaining this certification, you are in a more favorable position than your competitors in the market. This opens up huge business opportunities for you.
Lower expenses for the organization: ISO 27001 certification help in checking any breach in data security. This saves huge costs that are associated with such breaches. In addition to that, implementing ISMS through ISO 27001 is much cheaper than the liabilities costs.
Better Organization: ISO 27001 certification requires proper documentation of the processes within the organization. This gives clarity among the workforce regarding the requirements of the certification and makes them more involved, thereby making the organization better.
The compulsory requirements for ISO 27001 Certification are listed in its sections from 4 to 10 – this implies every one of those prerequisites must be actualized in an organization to implement a standard ISMS.
Section 4: Context of the organization – This section talks about understanding the requirements of your organization for implementing an ISMS. This includes the identification of internal and external issues, the expectations of interested parties, identifying the right processes requirements for implementing ISMS, and defining the scope of ISMS for your organization.
Section 5: Leadership – The leadership requirements say that the top management is responsible and instrumental in implementing ISMS. The commitment to ISMS can be demonstrated through defining and communicating environmental policy, assigning the roles and responsibilities as well as establishing effective communication throughout the organization.
Section 6: Planning – The ongoing function of the ISMS should be planned by the top management. There should be an assessment of the risks and opportunities of the ISMS in the organization. This helps in identifying the objectives of the organization and planning for its accomplishment. It is very important for an organization to make an assessment of the environmental impact of their processes, as well as their legal obligations.
Section 7: Support – The support section deals with the management of all resources for the EMS. It includes requirements around competence, awareness, communication, and controlling documented information (the documents and records required for your processes).
Section 8: Operation – The operation requirements deal with all the environmental controls required by the business processes. It also includes the identification of potential risks and planning the mitigation responses in the event of such emergencies.
Section 9: Performance evaluation – It is done to verify your ISMS through monitoring and measurement. It includes assessment of your environmental compliances, internal audits, and management review of your ISMS.
Section 10: Improvement – This section deals with all the actions that can be taken in order to ensure continual improvement. It assesses process nonconformities and identifies the corrective actions for the processes.